
Genymotion is so far my favorite Android emulator. It’s both powerful and easy to use. It’s widely used by developers because it’s way faster than Android Studio emulator. Genymotion instances work right out of the box, however there are quite a few steps to set it up for smooth application pentesting and intercepting traffic with Burp.
Before we begin, Genymotion is based on VirtualBox. So you can preinstall it prior to setting up the emulator.
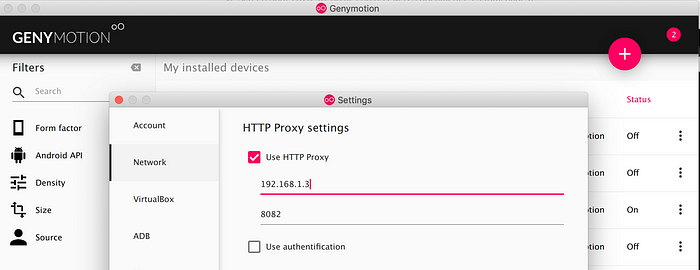
Once you go through the installation process, you can setup a proxy for all the future virtual devices. It can be done in Genymotion -> Preferences -> Network -> Use your host machine IP and a port(different from your Burp Proxy port).
Next, create a new virtual device.
Once the device is up and running, you will need to install GApps from the emulator toolbar on the right. Then find the appropriate version of ARM Translation Installer, drag and drop it to the home screen and reboot the device.
Now you can login to the Google Play with your account, but you can also drag and drop .apk files directly to home screen.
Once the basic setup is done, we can continue to setting everything up for traffic interception. We need to do 2 things: add proxy and Burp certificate to the device.
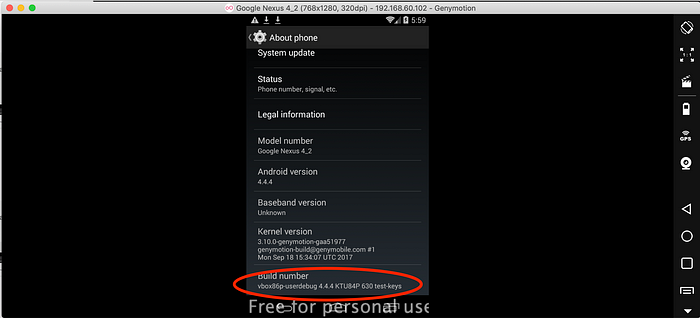
First, turn the developer mode on. It will give you access to additional features on the device.You can do it by going into Settings -> About phone -> and click a few times on Build number. You should see a popup letting you know when the mode is on.
Create new network:
Wi-Fi -> Add new Network -> click “Show advanced settings”. Then choose Manual for proxy and add your host machine IP and a port.


- In Burp Proxy settings add second proxy as your IP and the same port.

Adding Proxy:
Download Burp certificate to your local machine by going to http://burp on the browser you already use to intercept traffic with Burp.
- Change the cert extension from
.derto.cer.Otherwise the emulator won’t be able to read it. - Serve it from you host machine .

- Access it in the browser of your virtual Android device and download the
.cerversion of the cert.
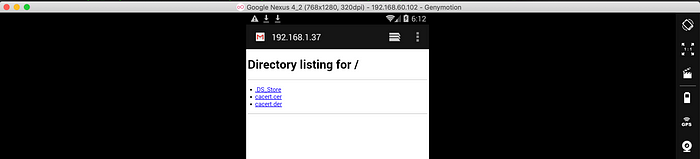
As an alternative, you can also go to
http://burpdirectly from you device browser and change the certificate extension from the Emulator’s Download folder. Ether way should work.
- Go to
Advanced Wi-Fi Settingsand add the cert for both,Wi-Fiandapps/VPN.

That’s it! You should see the traffic coming through your Burp Proxy at this stage.
Profit!
Bitcoin tip jar: bc1qgpl6lhf09j6kcdvkh8cz90p4cfxuyfec3ecjrd
Ethereum tip jar: 0x7e0Bf6D50b5F5fcbf76A16Bd5285CE0c74C063a9









